With a nearly 30% annual increase, cyber attacks affect one in five companies, and the average cost of such an infringement is around 13 million dollars. While the United States remains the main target for cybercriminals, France ranks fourth in this unfortunate tally. The issue of data protection has become a major concern, to the extent that the IAM (Identity and Access Management) market is expected to grow by nearly 23% over the next four years, according to ResearchAndMarkets.
Key players such as AS Cognito, MS AD (Microsoft Active Directory), ForgeRock, Sail Point, and Okta mainly deal with audit, compliance, and governance issues, directory services, multifactor authentication, provisioning, password management, and single sign-on. The house is well-guarded, similar to a hotel where rooms are protected with four-point locks, pervasive video surveillance, motion detectors, and a deterrent alarm.
However, you would agree, if at reception the hostess gives you the key to someone else’s room, all these protections become null and void, and you could raid your neighbor’s mini-bar without footing the bill.
The issue of knowing who is who and who has access to what at any given moment becomes a central topic that requires you to be up to date in real-time with your application mapping, regardless of the number of your employees (whether internal or external) and the number of applications used by your organization (typically several hundred cloud services).
In practice, however, only a third of companies are able to produce this application mapping within 24 hours. The responsibility is shared between the IT Department and the services, and it is difficult to blame someone who might have missed an email or a ticket or someone who, caught up in their activities, might have forgotten to request the withdrawal of a right.
Without centralized responsibility, automatic synchronization, or shared knowledge, there can be no satisfactory solution. Currently, ITSM tools that come to the aid of IAM tools only perform if an initial manual action is taken, provided they cover the full scope in coherence with the Human Resources Information Systems (HRIS), directory, and other tools for tracking non-salaried actors. In any case, and regardless of the depth of provisioning, they never indicate the reason for access, which significantly reduces audit capability.
ROK is designed around an organic and systemic approach to your organization supported by a unique disruptive algorithm (ROKe TM).
The organic axis will allow you to model your organization charts in integrity with your HRIS and directories, adding non-salaried collaborators if necessary; a digital who’s who that is up-to-date will thus be consultable and editable at any time for assured sharing. See who’s who article.
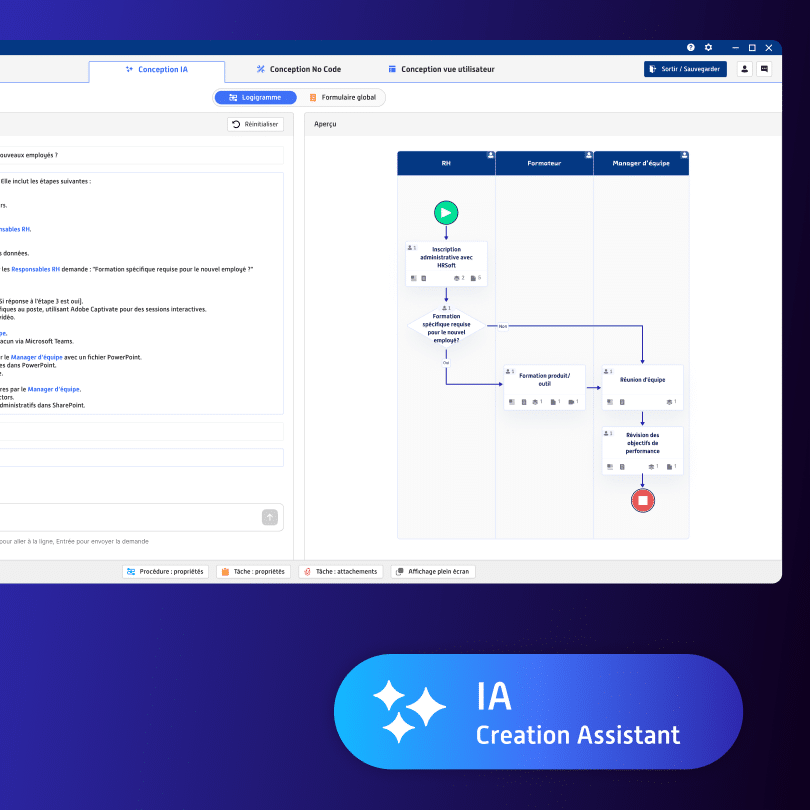
The systemic axis consists of a NoCode platform that will enable you to design your employee flows around these organization charts to track movements in entry, exit, and mobility as close as possible to your business specificities. The solution will feature connectors to ensure integrity with existing management software (HRIS, directories, ITSM …). Provisioning of rights will be ensured when it is not supported by another solution. See No Code article.
For example, ROK successfully provisions SAP across a scope of 200 sites covering all of Europe for the Elis group.
Testimonial from François Blanc – DSI at Elis
“ROK allows the standardization of access rights … the delegation of this management to the functions … the improvement of information system security, the reduction of administration costs.”
Overall, the implementation of your organizations, regardless of their complexity, as well as the synchronization rules with your existing supports, can be completed in just a few days (depending on your supports). Once this preliminary work is done, any movement of an employee will be followed in real-time.
Your application mapping will be managed in project mode directly via the platform. The provisioning work will be accelerated by the AI attached to the solution. In just a few weeks, any movement of an employee, or a method of work, will trigger the automatic update of the related application rights.
As a bonus, the solution will natively manage SOD (Segregation of Duties).
Technically, it is a multi-tenant, multi-instance cloud platform accessible on any laptop and mobile through a responsive web interface distributed directly in SaaS mode for less than 5 € per user or via our reseller ATOS.
After ten years of development, the ROK platform becomes the first No-Code platform “compliant” and secured by design, allowing you to model your organizations and, at the same time, to create your own applications in no-code, thus creating a unique link between the organic (your teams), the systemic (your flows) for a centralized shared vision of responsibilities and application rights.
ROK Decoder: Your Questions, Our Answers!
The IAM has never been so clear.
There are several ways to approach the topic of security, what are they?
There are several approaches, each presenting advantages and disadvantages:
- The restrictive methods that are Zero trust, the principle of least privilege (PMP) supplemented by PAM (Privileged Access Management). The advantage of these methods lies in the reduced attack surface exposure. The disadvantage resides in the complexity of implementation and maintenance but also in significant related costs combined with reduced performance.
- Role-Based Access Control (RBAC), which simplifies management except in the case of complex environments in the absence of organizational data.
Additionally, we can add:
- Dual control methods such as Multi-Factor Authentication (MFA) or Risk-Based Authentication (RBA) which is constraining for the first and complex for the second, which also requires continuous monitoring. Moreover, it is a method that does not suffice on its own.
If the RBAC method seems to be the most suitable, it quickly becomes apparent that given the size or complexity of the Group to be protected, its real-time update will pose a real issue, explaining why only 1/4 of companies are capable of producing an up-to-date application mapping within 48 hours.
How does ROK approach this topic? What method is used?
In ROK, access or permissions are granted to users based on their role within the organization, which simplifies permission management and improves security by limiting access to necessary resources.
This is close to RBAC (Role-Based Access Control); however, ROK goes beyond the notion of ‘role-based authorization’ and this is what makes it a unique offer that is simpler to implement and maintain, suited to complex environments with nuanced access requirements. To fulfill this promise, ROK presents three specifics not found in other IAM market offers:
- A merger of ‘authorization roles’ and ‘organizational roles’ which allows a single interface to integrate HRIS with IAM and automate iTsm.
- Real-time and automated management of employee flows through its No-Code module.
- Effortless integration of risks related to SoD (Segregation of Duties). Through its holistic approach, ROK will enable the use (interfacing) of preexisting tools in the company (IAM, directories, etc.) to orchestrate real-time information system security.
What effort is required to implement ROK?
ROK is a multi-tenant and multi-instance Cloud platform that can be served by a private or public cloud. Generally marketed as a SaaS for a unit cost of less than €5 per user, the platform’s provision is ‘instantaneous’.
Organizational setup is relatively quick if the information exists on one or more supports. The modeling of employee flows is simplified by AI and customizable to accommodate the specificities of important complex organizations.
A quick POC allows upfront validation of the effort to be produced for 360° coverage.
Daily maintenance is minimized and focused on organizational change (acquisition, merger, etc.)
What level of provisioning is allowed by ROK?
In the absence of preexisting tools (IAM integrating WF and/or iTsm tools like Service Now), ROK can provision any application presenting APIs through customized no-code flows.
ROK can also trigger an iTsm tool via APIs, for example, as soon as it automatically identifies a movement of employees or a business organizational change.
For instance, ROK automates the provisioning of SAP rights and advantageously replaces IDM by automating the update process and presenting the authorizations in IT language with its business translation.
In this particular case, ROK also carries the SoD aspect without additional cost.
This performance has been recognized by Atos, which is a distributor of this offer.