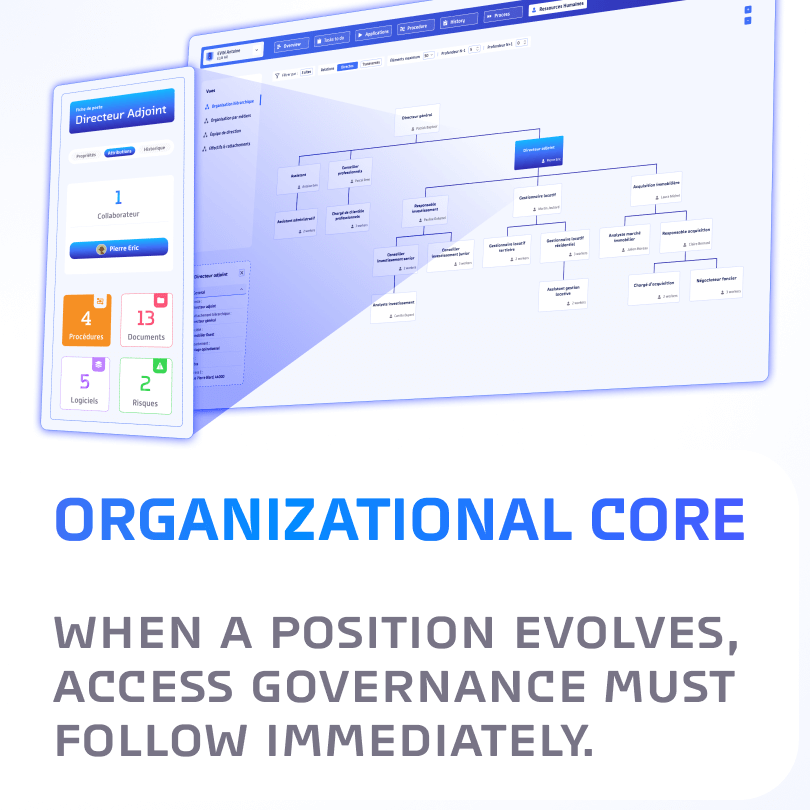
The org chart that governs IT access
When a role evolves, access governance must follow. Discover how ROK turns the org chart into a living foundation connecting roles, processes, and IT access.

When a role evolves, access governance must follow. Discover how ROK turns the org chart into a living foundation connecting roles, processes, and IT access.

Discover the special edition of the ROK Solution Chronicle: 5 years of evolution and innovation to unify governance and automation.
From no-code modeling to hyperautomation enhanced by generative AI, every milestone has strengthened our mission: helping organizations become more agile, autonomous and high-performing.
A comprehensive retrospective on ROK’s vision, progress and technology.
The Coding Bus tested ROK and created an HR onboarding application in just a few minutes with no-code. Discover how AI, workflows, and IAM/IGA come together in a single platform to automate your business processes.
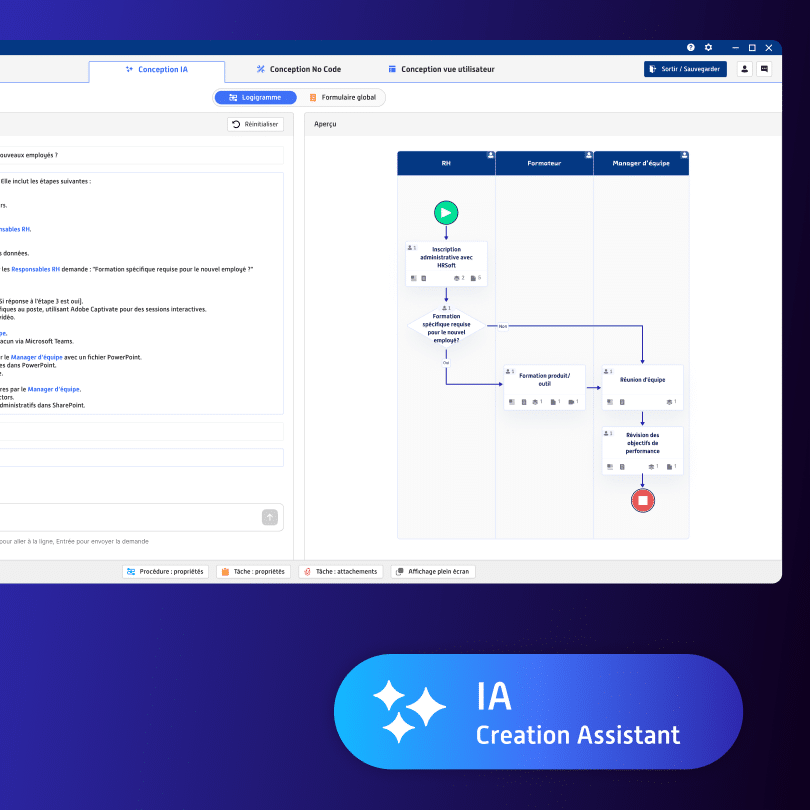
In the era of digital transformation, businesses of all sizes are seeking solutions to automate and simplify their business processes without requiring massive investments in development. ROK Solution offers an innovative no-code platform with AI that meets this need by integrating generative AI. This advanced technology enables companies to quickly and easily create custom business applications and transform their organization in an intuitive, fast, and secure manner, tailored to their digitalization needs. A No-Code platform with AI for accelerated digital transformation ROK Solution is a automation platform integrating generative AI, enabling the creation and management of complex business processes without requiring technical skills. Unlike traditional platforms, ROK offers an intuitive experience by allowing users to model workflows and generate applications simply by describing their needs in natural language. Through this approach, ROK Solution’s AI automatically creates tailored solutions, helping businesses optimize their processes while reducing the costs and timelines associated with traditional development methods. Quick creation of applications and workflows with integrated AI One of the strengths of ROK Solution lies in its ability to create business applications in no-code, powered by generative AI, in record time. While other solutions often require days or weeks to configure an application, ROK Solution enables the creation of ready-to-use applications in just minutes, thanks to workflow automation powered by generative AI. This no-code platform for rapid automation automatically configures workflow steps, assigns roles, and connects necessary tools for smooth and optimized operations. With ROK Solution, businesses can deploy applications across various departments, such as human resources, procurement, or identity management. Optimized workflows reduce teams’ workload, allowing employees to focus on higher-value tasks and fostering a productivity boost. Flexibility and management of applications and workflows The flexibility of managing applications and workflows sets ROK Solution apart from other platforms. It allows businesses to manage multiple applications and workflows from a single interface, without the need to reconfigure permissions and access rights. ROK understands your organization, assigning user rights based on their roles, without requiring complex setup. This solution offers simplified access management, enabling companies to quickly adapt to operational needs while ensuring secure and seamless process management. Simplified automation of roles and permissions Workflow optimization is at the core of ROK Solution. By integrating automated access rights management with AI, ROK Solution simplifies the organization of business processes. Each user is assigned rights and permissions based on their role, eliminating the need for manual configurations for each project. This automation of business processes with generative AI is particularly valuable for companies with complex structures and varying access levels, ensuring consistent and secure management of internal processes. Data security and compliance with standards Data security is a critical pillar for modern businesses, especially in highly regulated sectors such as finance, healthcare, and public services. ROK Solution is designed to meet the strictest security standards, ensuring that all processed data is protected. This no-code platform, compliant with cybersecurity regulations, provides peace of mind to companies looking to digitalize their processes while maintaining robust protection of sensitive information. A digital transformation solution tailored to businesses of all sizes Whether you’re an SME or a large enterprise, ROK Solution provides a no-code platform powered by AI, designed to digitalize your business processes and meet the specific needs of any organization. Leveraging generative AI and automation, this solution simplifies application creation, accelerates digital transformation, and enhances team productivity. Accessible to everyone, even without programming skills, ROK makes digitalization faster, more affordable, and more efficient, helping you optimize your operations. In summary ROK Solution is more than just a no-code tool; it’s a comprehensive platform for digital transformation, designed to help businesses automate, simplify, and secure their business processes. By integrating generative AI and offering unmatched flexibility in workflow management, ROK Solution empowers companies to tackle the challenges of modern digitalization. Optimizing operations and ensuring robust security, ROK Solution stands out as a key partner for organizations seeking to transform their business processes quickly and efficiently. To learn more about ROK Solution and discover how this platform can support your company in its digital transition, contact us today.
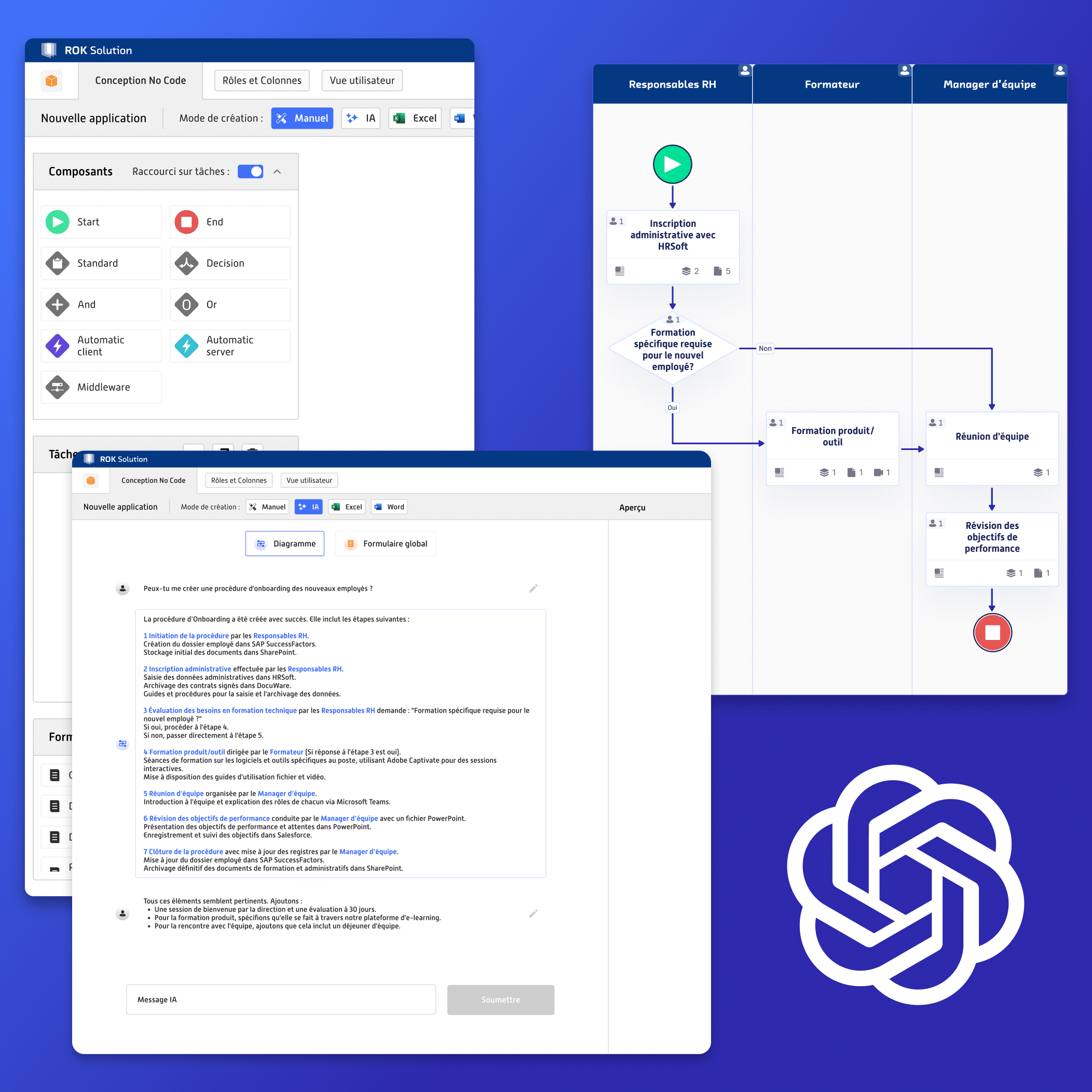
Faced with the need for workflow automation using no-code in businesses, many low-code and no-code solutions are emerging to simplify business processes. But in a saturated market, how can you choose the tool best suited to the complex needs of your organization? This comparison highlights ROK Solution, a unique platform that stands out for its integration of generative AI and its specialization in advanced workflows, as well as a few other well-known solutions, to help you evaluate the available options. ROK Solution: Workflow automation in No-Code with Generative AI for complex business processes ROK Solution offers an innovative approach combining no-code and generative artificial intelligence, enabling the modeling of even the most complex business processes. Unlike traditional platforms that often require technical expertise to configure workflows, ROK uses AI to assist users in creating applications through natural language. This functionality makes ROK particularly accessible to non-technical users and provides optimal flexibility for organizations seeking to automate complex processes with continuous, real-time improvements. Key Features: Automation of authorizations: ROK facilitates the management of application and hardware access based on roles and organizational changes, assigning tasks by position. This real-time management provides enhanced control over access, making it ideal for comprehensive IAM (Identity and Access Management). Intuitive workflow creation: Thanks to generative AI, users can create and manage workflows using simple natural language instructions, enabling rapid responses to business needs without requiring specialized developers. Use cases by sector: ROK Solution, flexibility for complex needs 1. Human Resources Management of recruitment, departures, and job changes, with automatic updates of access and permissions based on the organizational chart, covering both internal employees (endogenous) and external partners (exogenous). Tracking of training, skills, and certifications, with automatic assignment of necessary application and hardware access based on roles. Automation of validation processes for leave or time-off requests, performance evaluations, and other HR processes, fully integrated in real-time with the HRIS to ensure data integrity. 2. Finance and Procurement Multi-level validation for orders, invoices, and other financial transactions, incorporating strict access controls based on hierarchical levels and identity verification procedures (KYC) to ensure compliance and transaction security. Automation of document management with integrated OCR to extract key information from financial documents. Automated reporting and real-time budget tracking, simplifying transparency and financial flow analysis. 3. Security and Access Management Centralized control of access to IT systems and sensitive data, with real-time traceability. Implementation of a robust IAM (Identity and Access Management) system that adjusts access rights based on internal or external movements, ensuring optimal security. Real-time monitoring of access rights, allowing verification of who has access to which data and applications, ensuring regulatory compliance. 4. Production, Logistics, and Compliance Automation of workflows for inventory management, supplier orders, and shipment tracking. Optimization of preventive and corrective maintenance through automated workflows that assign tasks to maintenance teams based on urgency and availability, while ensuring compliance with applicable regulations (such as DORA, GDPR, and other security and privacy standards). Management of quality controls by automating procedures and integrating inspection data for complete traceability. Case study: global resource and access management for a multinational corporation One of ROK Solution’s clients, operating in 23 countries with 43 production plants and 6,000 employees, uses ROK to centralize and manage its entire organizational structure. With ROK, this company seamlessly tracks employee onboarding and offboarding, job changes, as well as access to associated applications and equipment. Updates are automatically synchronized with HRIS systems and electronic directories, adjusting in real time to internal movements. This centralization ensures optimal traceability and security while streamlining the assignment of tasks and responsibilities based on roles, providing unparalleled organizational agility. Comparison with other market solutions To position ROK Solution in the context of workflow automation platforms, here is an overview of some popular solutions and their specific features: IBM Business Automation: A powerful solution for companies with BPM (Business Process Management) needs, integrating RPA, but often complex to implement and more suited for technical teams. Appian: A comprehensive low-code platform with a wide range of features, but expensive and often requiring technical support for configuration. ServiceNow: Renowned for IT process management and simple workflows but less flexible for complex business processes. Nintex: Easy-to-use platform for standard workflows, but may reach its limits for companies with advanced authorization and security needs. Camunda: An open-source BPM solution ideal for developers but lacking the no-code accessibility and integrated AI assistance that ROK offers. Comparative Summary: While other solutions often require advanced technical skills and complex configurations, ROK Solution enables organizations to manage complex workflows in a simple and accessible manner. By leveraging AI to streamline process configuration and role management, ROK ensures real-time security and access traceability, providing a complete and intuitive solution for users. Integrated OCR functionality at no additional cost In addition to its advanced workflow automation features, ROK Solution natively integrates optical character recognition (OCR). This feature is particularly useful for companies handling large volumes of documents requiring automated data extraction, such as in financial services or HR departments. Unlike other platforms that may require third-party modules or software for OCR, ROK includes it as part of its core solution, thereby simplifying document management. Optimized cost: A cost-effective alternative for workflow automation ROK Solution also positions itself as a cost-effective option for companies aiming to centralize and automate their business processes without exceeding their budgets. With a more affordable licensing structure and maintenance compared to competing platforms like PowerApps, ROK enables significant savings, costing on average only 2 to 3 euros per user per month. By minimizing reliance on third-party tools and reducing training needs, ROK offers excellent cost-efficiency, particularly for large organizations with advanced workflow management requirements. Onboarding, support, and training services for optimal adoption To support companies in getting started with the platform, ROK Solution offers comprehensive onboarding, technical support, and training services. These services enable users, whether technical or non-technical, to fully leverage the platform’s advanced features, ensuring a smooth transition and successful deployment of the tool. Conclusion: Which solution to optimize your business processes? In conclusion, ROK
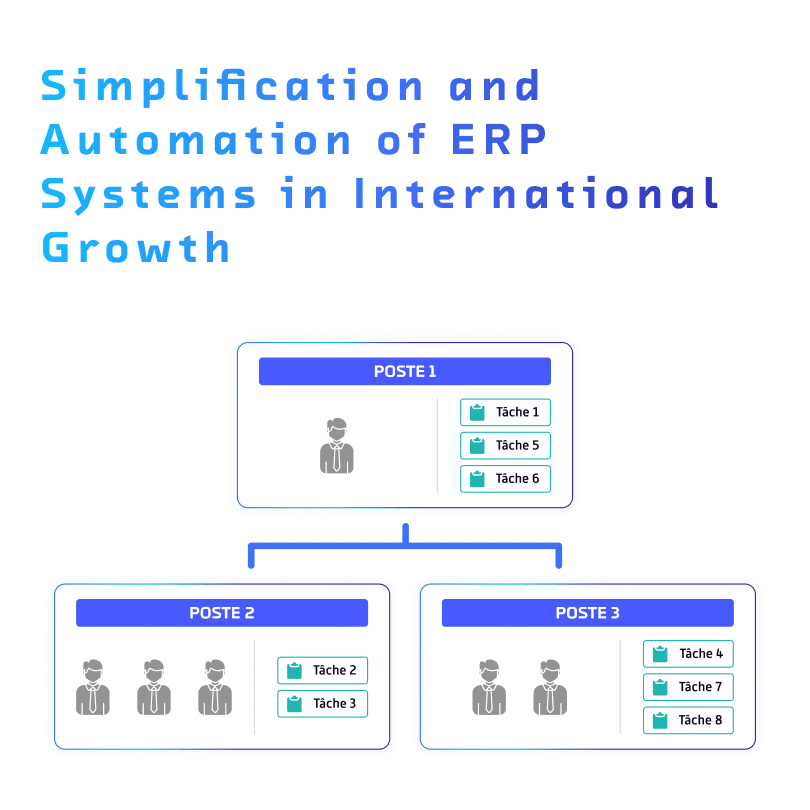
Centralization and security of SAP access at scale International companies face increasing complexity in managing SAP access. To address these challenges, a solution like ROK centralizes and secures access, enhancing security, ensuring compliance, and optimizing costs. Challenges of rapid expansion Rapid growth: presence in multiple countries and a large number of employees across various sites, complicating SAP access management. SAP access security: ensuring secure and compliant access management for thousands of employees. Automation: automating role updates to minimize manual interventions. Cost reduction: centralizing access management and optimizing ERP costs. Measured results (ROI) 10x cost reduction Automated SAP access administration. 10x more scope Managed without staff increase. 5x shorter timelines SAP authorizations delivered faster. < €1000 monthly cost Support cost lower than competing solutions. 100% integration/b> Centralized management via CUA or directly. Optimized and automated SAP access management Standardization & automation Unified model applied across multiple countries for consistent international processes. Real-time automation of hires, transfers, and departures. Traceability and role optimization for efficient and compliant management. Rapid integration of new entities Accelerated deployment of new acquisitions. Automated onboarding via SAP HR, with access assigned based on responsibilities. Strict authorization security during integration. Cost optimization Fewer errors thanks to automation. Optimized IT and HR resources, reducing workload. ERP streamlining with centralized updates and role management. Architecture: strength and flexibility of the ROK implementation The diagram illustrates the centralized architecture implemented to manage SAP access at Elis, ensuring smooth and secure authorization management across all SAP systems. Management of functions, positions, and employees with assignment and organizational restrictions. Import processing by ROK Transcription of roles into an organizational chart. Gestion des postes et collaborateurs (création, modification, archivage). Assignment of business roles and functional restrictions. Sending of authorization data by ROK Automatic synchronization of roles (composite, simple, derived). Quick rights assignment, with access delivered within 1 hour.

With a nearly 30% annual increase, cyber attacks affect one in five companies, and the average cost of such an infringement is around 13 million dollars. While the United States remains the main target for cybercriminals, France ranks fourth in this unfortunate tally. The issue of data protection has become a major concern, to the extent that the IAM (Identity and Access Management) market is expected to grow by nearly 23% over the next four years, according to ResearchAndMarkets. Key players such as AS Cognito, MS AD (Microsoft Active Directory), ForgeRock, Sail Point, and Okta mainly deal with audit, compliance, and governance issues, directory services, multifactor authentication, provisioning, password management, and single sign-on. The house is well-guarded, similar to a hotel where rooms are protected with four-point locks, pervasive video surveillance, motion detectors, and a deterrent alarm. However, you would agree, if at reception the hostess gives you the key to someone else’s room, all these protections become null and void, and you could raid your neighbor’s mini-bar without footing the bill. The issue of knowing who is who and who has access to what at any given moment becomes a central topic that requires you to be up to date in real-time with your application mapping, regardless of the number of your employees (whether internal or external) and the number of applications used by your organization (typically several hundred cloud services). In practice, however, only a third of companies are able to produce this application mapping within 24 hours. The responsibility is shared between the IT Department and the services, and it is difficult to blame someone who might have missed an email or a ticket or someone who, caught up in their activities, might have forgotten to request the withdrawal of a right. Without centralized responsibility, automatic synchronization, or shared knowledge, there can be no satisfactory solution. Currently, ITSM tools that come to the aid of IAM tools only perform if an initial manual action is taken, provided they cover the full scope in coherence with the Human Resources Information Systems (HRIS), directory, and other tools for tracking non-salaried actors. In any case, and regardless of the depth of provisioning, they never indicate the reason for access, which significantly reduces audit capability. ROK is designed around an organic and systemic approach to your organization supported by a unique disruptive algorithm (ROKe TM). The organic axis will allow you to model your organization charts in integrity with your HRIS and directories, adding non-salaried collaborators if necessary; a digital who’s who that is up-to-date will thus be consultable and editable at any time for assured sharing. See who’s who article. The systemic axis consists of a NoCode platform that will enable you to design your employee flows around these organization charts to track movements in entry, exit, and mobility as close as possible to your business specificities. The solution will feature connectors to ensure integrity with existing management software (HRIS, directories, ITSM …). Provisioning of rights will be ensured when it is not supported by another solution. See No Code article. For example, ROK successfully provisions SAP across a scope of 200 sites covering all of Europe for the Elis group. https://www.youtube.com/watch?v=OBtGHALwPB0 Testimonial from François Blanc – DSI at Elis “ROK allows the standardization of access rights … the delegation of this management to the functions … the improvement of information system security, the reduction of administration costs.” Overall, the implementation of your organizations, regardless of their complexity, as well as the synchronization rules with your existing supports, can be completed in just a few days (depending on your supports). Once this preliminary work is done, any movement of an employee will be followed in real-time. Your application mapping will be managed in project mode directly via the platform. The provisioning work will be accelerated by the AI attached to the solution. In just a few weeks, any movement of an employee, or a method of work, will trigger the automatic update of the related application rights. As a bonus, the solution will natively manage SOD (Segregation of Duties). Technically, it is a multi-tenant, multi-instance cloud platform accessible on any laptop and mobile through a responsive web interface distributed directly in SaaS mode for less than 5 € per user or via our reseller ATOS. After ten years of development, the ROK platform becomes the first No-Code platform “compliant” and secured by design, allowing you to model your organizations and, at the same time, to create your own applications in no-code, thus creating a unique link between the organic (your teams), the systemic (your flows) for a centralized shared vision of responsibilities and application rights. cyberexperts.tech digit-collab.com decideur-it.fr ntic-infos.fr disrupt-b2b.fr dsi-numerique.fr numeric-tools.com actu-dsi.fr itb2b-univers.com dsisionnel.com ROK Decoder: Your Questions, Our Answers! The IAM has never been so clear. There are several ways to approach the topic of security, what are they? There are several approaches, each presenting advantages and disadvantages: The restrictive methods that are Zero trust, the principle of least privilege (PMP) supplemented by PAM (Privileged Access Management). The advantage of these methods lies in the reduced attack surface exposure. The disadvantage resides in the complexity of implementation and maintenance but also in significant related costs combined with reduced performance. Role-Based Access Control (RBAC), which simplifies management except in the case of complex environments in the absence of organizational data. Additionally, we can add: Dual control methods such as Multi-Factor Authentication (MFA) or Risk-Based Authentication (RBA) which is constraining for the first and complex for the second, which also requires continuous monitoring. Moreover, it is a method that does not suffice on its own. If the RBAC method seems to be the most suitable, it quickly becomes apparent that given the size or complexity of the Group to be protected, its real-time update will pose a real issue, explaining why only 1/4 of companies are capable of producing an up-to-date application mapping within 48 hours. How does ROK approach this topic? What method is used? In

In the era of the digital enterprise, the ability to instantly visualize its internal and external organizational structure through accurate, editable, and real-time maintained charts is fundamental. This requirement aims to place the individual at the heart of the information system, with the goals of clearly identifying roles and responsibilities, allocating necessary digital resources, and optimizing business processes while securing the organization and its information system. To date, no platform integrates in a single offering the real-time integration of organizational charts and authorization charts, the integration of workflow tools needed to manage employee flows, or iBPMs to work on optimizing existing processes in dynamic environments with shifting organizations. Even so, some solutions specialized in human resources management (HRIS) or identity and access management (IAM) partially meet these needs (often in conjunction with other tools) (1), the challenge of maintaining this information up-to-date in real time remains significant. According to Gartner, 75% of companies cannot provide a real-time mapping of permissions. It is also rare to see charts that dynamically integrate both vertical and transversal hierarchical dimensions, both endogenous and exogenous. In this context, ROK stands out as an innovative platform that has developed a unique concept of integrated position modeling in NoCode, allowing for the merger of organizational roles (HRIS) and permissions (IAM). This approach greatly simplifies the maintenance of real-time data integrity with various directories and tools already in place. Organization: Modeling & Monitoring of Flows with Who’s Who (rok-solution.com) ROK can be positioned upfront to manage employee movements through efficient onboarding flows (modeled in NoCode) and dispatch information in real time to the HRIS, existing ITSM directories, or IAM in place. Depending on company policies, ROK can also be used as a central hub consolidating various digital entries, bridging gaps and offering a simple orchestration interface. Onboarding, management of assets and application rights (rok-solution.com). The platform, mainly available as SaaS at about €5 per user, can also be offered as an on-premise solution depending on specific needs. ROK offers a responsive web interface and can be deployed (in multi-tenant and multi-instance) on any type of cloud, public or private. Mr. Pierre Boulet, CEO of Novares Group (an automotive supplier that employs 10,000 people across more than 20 countries, 37 production sites, 7 technical centers, and 6 centers of expertise) testifies: “Managing an international group requires daily management of a diversity of cultures and backgrounds. When making acquisitions, it is crucial to integrate different cultures into the most harmonious whole possible. The HR challenge is daily. Implementing ROK is a formality in these processes that allow our employees to position themselves in the organization both at their level and that of their colleagues, which is crucial in a group structure. Today ROK is considered our cornerstone, it is an HR database therefore everything we do is based on it. It meets the need and is fully embedded in our business processes. For example, all the company’s workflows (IN – OUT – MOVE) are managed from ROK, and the visualization part is very used. The solution also allows us to manage the allocation of assets, standardize hiring circuits, and manage delegation of authority, thus eliminating many frustrations among our employees. This solution, deployed in all countries to a very diverse population because its interface is accessible with simple training, has ended up being adopted by HR, even the most reluctant ones.” Novares: Organizational management at the heart of the automotive industry (rok-solution.com) ROK thus positions itself as an original and comprehensive response to the challenges of organizational management and information security for contemporary businesses, marking a significant evolution in how companies can orchestrate their application rights and organizational structure dynamically with minimal effort and cost. (1) Workday HCM, Microsoft 365 HR, Oracle HCM, SAP SuccessFactors combined with SAP Cloud IAM… for the most complete solutions, however, they are rarely simple to implement and often require additional modules or third-party integrations. ia-news.fr digit-collab.com esn-news.fr marketing-numeric.fr decideur-it.fr cloudmagazine.fr ntic-infos.fr disrupt-b2b.fr dsi-numerique.fr www.numeric-tools.com actu-dsi.fr carrefourdusaas.com itb2b-univers.com dsisionnel.com ROK Decoder: Your Questions, Our Answers! The Who’s Who has never been so clear. What does ‘Who’s Who’ mean? The who’s who, as seen by ROK, is a graphical representation that allows you to visualize through multiple charts who is who and also who does what, with which tools (Document Management Systems and Applications) and what risks are involved. This visual directory is integrated in real-time with your Active Directory (AD), your HR Information System (HRIS), Identity and Access Management (IAM), etc. It manages and allows you to visualize both hierarchical and lateral links and can be printed. It is multi-company and also allows you to integrate your ecosystem of partners (subcontractors, temporary workers, consultants). It is dynamically maintained in real-time and can interface with your application ecosystem to provision and maintain up-to-date authorizations. In the same vein, it allows you to edit job descriptions or manage your Outlook mailing lists (or other email systems) in real-time. It is a true 360-degree control tower of your organization. How do we ensure that the charts are up-to-date in real-time? ROK incorporates a No Code module that allows you to propose onboarding, moving, and outboarding flows close to your specific needs and also to connect with your application ecosystem via web services (AI-assisted modeling). You can choose to see ROK as the hub for employee movements and let it automatically update your HRIS, IT Service Management (ITSM), IAM, or use it as a hub collecting information from these various sources (often multiplied in groups) to orchestrate them; in the latter case, you would complement (unaccounted ecosystems or orphan subsidiary applications) the untreated information by quickly and easily creating the necessary collection apps through the No Code module. How do we visualize, print, and understand complex and numerous organizations? The charts in ROK are multi-indexed; you can thus view them according to the axis of interest at any given moment by presenting them by: company, site, department, function, business unit, product line, market,

ROK Solution is referenced in the “RMIS PANORAMA Risk Management Information Systems” Edition 2022
We use cookies to optimize your visit on our website. Accept to continue or manage your preferences.