IGA:
Dynamic orchestration of roles, identities, and access for enhanced security and compliance
360° on Governance and Access Management
✓ Authorize the right people to access the right resources, at the right times, for the right reasons.
✓ Do not exclude any software or any actor.
✓ Provision your IS in real time.
Take real-time control of
100% of access to your IT systems
Because ROK models your organizations and workflows with the same ease, it’s simple and fast to map and maintain the completeness of employee and partner accesses.
Map your application accesses
ROK offers you the simple collection, centralization, mapping, and orchestration of your users and applications, whether internal or external, regardless of the complexity of your organizations or the dispersion of your collaborators.
Organization collection

+ Software inventory

= Attribution matrix

Real-time monitoring and control
Provision
100% of your application permissions
You likely have ITSM tools to accelerate the provisioning of your critical application rights, but their functional coverage remains incomplete and relies too heavily on the discipline of your employees.
Integration with your HRIS and electronic directories
Automated utilization of your pre-existing ITSM workflows
Integrated creation of appropriate in, out, and move workflows to complement your coverage
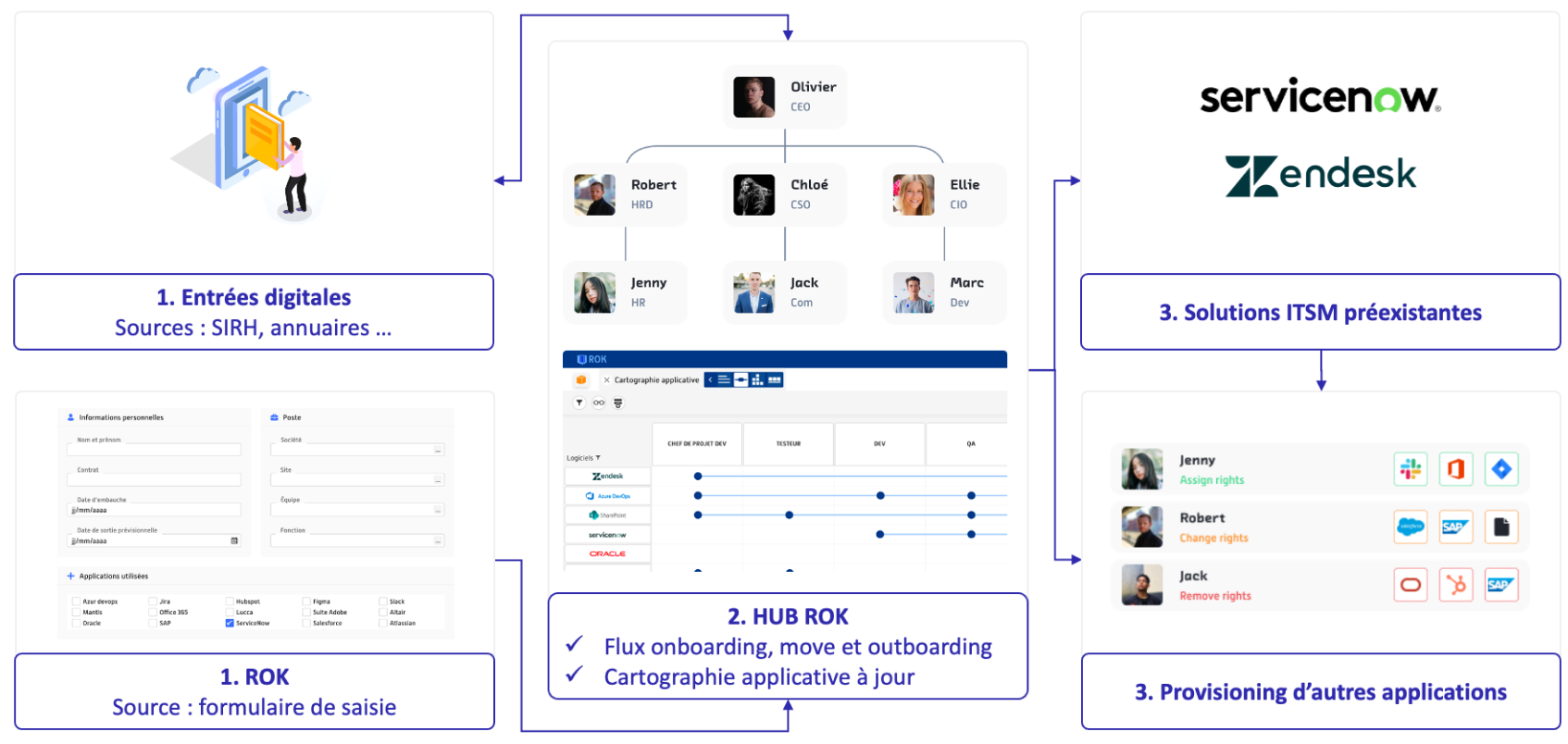
Make all your accesses systematic and real-time effortlessly, while maintaining what already works… without neglecting the complexity of your organization, your businesses, or your partner ecosystem.
Control of
Risk and Compliance
Integration of SoD
Dynamic access and risk management thanks to ROK’s unique concept.
360° Reporting
Use every feature of ROK as a sorting or selection criterion.
Risk mapping
Use APIs to report on the main BI tools in the market.
Audit process
Create your own risk audit campaigns.
Manage SAP authorizations and licenses
along with SoD
Authorization automation
- Provisioning based on SIRH organizational movements
- Automatically create/modify/derive roles
- Creation/Modification/Deletion of users
- Assignments/Unassignments of composite roles to users
SoD controls monitoring capabilities
- Real-time SoD analysis at the level of simple, derived, composite roles, and at the user level (integrated with HRIS)
- Steering and execution of compensatory controls via workflows
- Integrated risk module in ROK
SAP license management
- In alignment with HRIS organizational movements
- "Manage your SAP licenses accurately in real time
- Ensure audit-compliant licenses
✓ Functional coverage: SAP IDM / Acces Control / SAP SoD
✓ Scope: SAP HR / SAP BPC / SAP Fiori / SAP ECC / SAP BW
Access management for
Documents and Processes
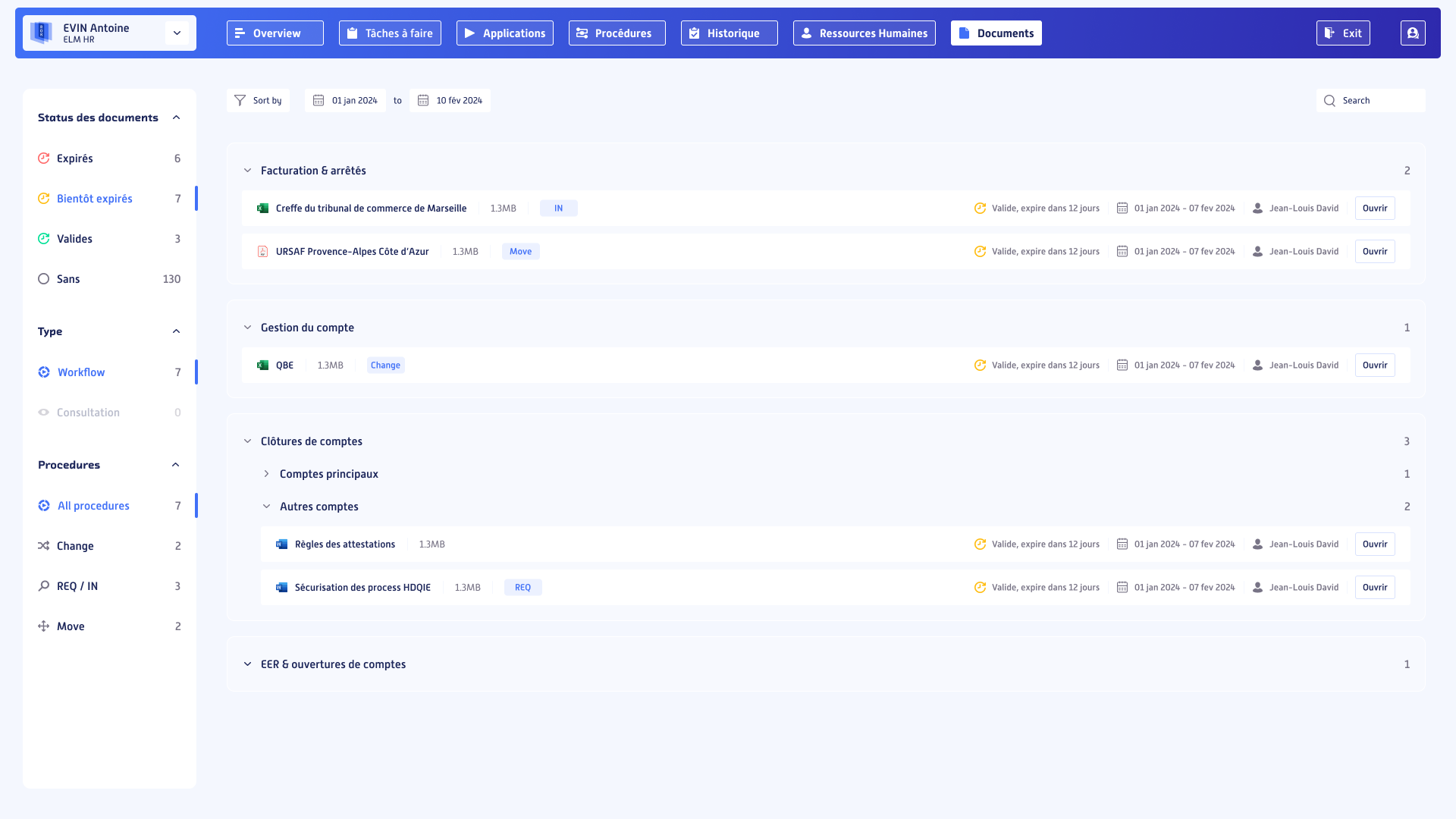
Document lifecycle management
Tracking and updating documents to ensure their compliance.
Secure access to the Document Management System
Access the appropriate documents in real time, regardless of the data source.
Secure access to processes and operating procedures
Accès personnalisé pour chaque collaborateur à ses processus spécifiques.
ROK Decoder:
Your Questions,
Our Answers!
The IAM has never been so clear.
There are several ways to approach the topic of security, what are they?
There are several approaches, each presenting advantages and disadvantages:
- The restrictive methods that are Zero trust, the principle of least privilege (PMP) supplemented by PAM (Privileged Access Management). The advantage of these methods lies in the reduced attack surface exposure. The disadvantage resides in the complexity of implementation and maintenance but also in significant related costs combined with reduced performance.
- Role-Based Access Control (RBAC), which simplifies management except in the case of complex environments in the absence of organizational data.
Additionally, we can add:
- Dual control methods such as Multi-Factor Authentication (MFA) or Risk-Based Authentication (RBA) which is constraining for the first and complex for the second, which also requires continuous monitoring. Moreover, it is a method that does not suffice on its own.
If the RBAC method seems to be the most suitable, it quickly becomes apparent that given the size or complexity of the Group to be protected, its real-time update will pose a real issue, explaining why only 1/4 of companies are capable of producing an up-to-date application mapping within 48 hours.
How does ROK approach this topic? What method is used?
In ROK, access or permissions are granted to users based on their role within the organization, which simplifies permission management and improves security by limiting access to necessary resources.
This is close to RBAC (Role-Based Access Control); however, ROK goes beyond the notion of ‘role-based authorization’ and this is what makes it a unique offer that is simpler to implement and maintain, suited to complex environments with nuanced access requirements.
To fulfill this promise, ROK presents three specifics not found in other IAM market offers:
- A merger of ‘authorization roles’ and ‘organizational roles’ which allows a single interface to integrate HRIS with IAM and automate iTsm.
- Real-time and automated management of employee flows through its No-Code module.
- Effortless integration of risks related to SoD (Segregation of Duties). Through its holistic approach, ROK will enable the use (interfacing) of preexisting tools in the company (IAM, directories, etc.) to orchestrate real-time information system security.
What effort is required to implement ROK?
ROK is a multi-tenant and multi-instance Cloud platform that can be served by a private or public cloud. Generally marketed as a SaaS for a unit cost of less than €5 per user, the platform’s provision is ‘instantaneous’.
Organizational setup is relatively quick if the information exists on one or more supports. The modeling of employee flows is simplified by AI and customizable to accommodate the specificities of important complex organizations.
A quick POC allows upfront validation of the effort to be produced for 360° coverage.
Daily maintenance is minimized and focused on organizational change (acquisition, merger, etc.)
What level of provisioning is allowed by ROK?
In the absence of preexisting tools (IAM integrating WF and/or iTsm tools like Service Now), ROK can provision any application presenting APIs through customized no-code flows.
ROK can also trigger an iTsm tool via APIs, for example, as soon as it automatically identifies a movement of employees or a business organizational change.
For instance, ROK automates the provisioning of SAP rights and advantageously replaces IDM by automating the update process and presenting the authorizations in IT language with its business translation.
In this particular case, ROK also carries the SoD aspect without additional cost.
This performance has been recognized by Atos, which is a distributor of this offer.
Go ahead and get started right now!
Learn more: Dynamic orchestration of roles, identities, and access
Dynamic orchestration of roles, identities, and access: secure your applications and your IGA
Dynamic orchestration of roles, identities, and access has become a strategic necessity for organizations seeking security, compliance, and agility. As IT infrastructures become increasingly hybrid and distributed, identity management can no longer rely on manual processes. It requires an automated, intelligent, and continuous approach that can adapt to evolving roles, users, and regulatory requirements.
With strong governance, each user is assigned rights based on their role, responsibilities, and environment. This logic is built on proven models like RBAC (Role-Based Access Control), enhanced by dynamic layers such as ABAC (Attribute-Based Access Control) and PBAC (Policy-Based Access Control). These mechanisms enable granular and contextual access control, taking into account user roles, attributes, and security policies.
The goal is to limit excessive privileges, ensure Separation of Duties (SoD), streamline access, and reduce risk. With IGA, companies can automate the entire user lifecycle—from onboarding to access revocation. Automated access provisioning keeps permissions up to date in real time while maintaining regulatory compliance.
This is an essential approach aligned with the principles of hyperautomation (workflow orchestration, BPM, RPA, AI, no-code).
Dynamic orchestration of roles, identities, and access: automated management, continuous security, native compliance
Dynamic orchestration of roles, identities, and access relies on real-time tools for traceability, auditing, and supervision. It ensures identity and access governance in complex environments, while complying with standards such as GDPR, ISO 27001, and NIS Directive. Every user action is logged, every permission is auditable, and every exception is traceable.
Access certification can be performed at regular intervals without administrative overhead. Real-time IT access management functions allow rights to be granted or revoked based on activity, risk, or status changes. This level of precision is essential for reducing unauthorized access risks and mitigating insider threats.
Built-in access audit and traceability tools enable the automatic generation of actionable reports, aligned with regulator expectations. This capability is further strengthened by directory synchronization (AD, LDAP, Azure AD), ensuring consistency across identity sources—even in multi-domain or multi-entity environments.
This automation can be activated from the moment of integration with an onboarding automation and access management module, ensuring a secure lifecycle from day one.
Dynamic orchestration of roles, identities, and access: a lever of agility for ERP and business teams
Dynamic orchestration of roles, identities, and access goes beyond IT. It directly impacts business functions, critical applications such as ERP and SAP, and field users. Thanks to native integration with business information systems, the platform automatically adjusts rights, permissions, and roles according to the user’s actual role. This helps reduce shadow IT and strengthens operational efficiency.
Advanced features allow business access to be managed in line with established security policies. Each role can be simulated, tested, and validated before being assigned. Risk-based access management policies allow permissions to be adjusted based on contextual events—such as login from a new device, department changes, or unusual activity. The system can trigger alerts, blocks, or multi-level approvals.
The interface provides clear visibility into user identification, session management, and access history. It also supports native multi-factor authentication or integration with third-party solutions, ensuring secure remote access. This dynamic management helps reduce operational costs while enhancing both the user and security team experience.
This automated access control is also fully compatible with role automation and access management solutions for ERP and SAP.
Dynamic orchestration of roles, identities, and access: centralized governance, tailored policies, and multi-domain strategy
Dynamic orchestration of roles, identities, and access enables a centralized yet flexible identity governance strategy. It adapts to decentralized structures, multi-site organizations, and international groups. The model is based on customizable policies that can be applied by entity, department, or scope of action. It allows organizations to meet all regulatory requirements without added complexity.
Each entity can define its own access security policies while adhering to the standards set by the IT department or the CISO. The integration of identity management systems ensures consistency across application layers and enables smooth identity management across multiple directories. This flexibility is key to supporting IT change management projects, mergers, or structural transformations.
All these capabilities can be enhanced with sector-specific connectors. For example, in the banking sector, access security and regulatory compliance for financial institutions is strengthened by specific policies for traceability and risk management.
For such needs, direct integration with the dedicated solution for access security and regulatory compliance for financial institutions provides a proven and adaptable framework.
For a comprehensive strategy, organizations can rely on dynamic role and access management for secure IT governance to model tailor-made IAM processes that are secure and aligned with specific business contexts.