Automate your
internal audits
and manage risks through a structured framework
✓ Generate your audit missions and risk frameworks with AI-assisted No-Code.
✓ Manage your risks in real-time with dynamic mappings and KPIs.
✓ Gain traceability and compliance with enhanced security.
A proven methodology
and a structured framework
A framework designed to efficiently structure each stage of your audits, based on four key processes:
1
Mission preparation → Definition of objectives, planning, and role assignment.
2
3
4
Implementation of action plans → Monitoring recommendations, managing corrective actions, and evaluating results.

Anticipate and control your risks
with a structured management approach
With ROK, you benefit from a structured framework and powerful tools to secure your audit processes.
Map risks and ensure dynamic monitoring at every stage.
📺 Episode 1 - Packaged Referential Methodology
Discover how ROK enables you to use a structured framework to efficiently conduct your audit missions and map your risks.
Model and deploy your missions
with AI-assisted No-Code
Enjoy seamless and intuitive access to all your audits, wherever you are.
A flexible and intuitive environment to design audit processes tailored to your needs.
Easily organize your audits by adding or modifying steps and roles with drag-and-drop.
📺 Episode 2 - Quickly model your own missions
With ROK Solution, create and customize your risk management and audit applications without IT skills, thanks to AI-assisted No-Code.
Web user portal:
all your audit assignments in real time
Access your audits and missions in real-time through an intuitive web user portal.
A centralized workspace for efficient audit mission management.
Track your audits in real-time with KPIs and key indicators on an interactive dashboard.
Manage all your missions in one click with a centralized view and detailed tracking.
📺 Episode 3 - User Interface
Discover how the user portal simplifies audit tracking and management for your teams.
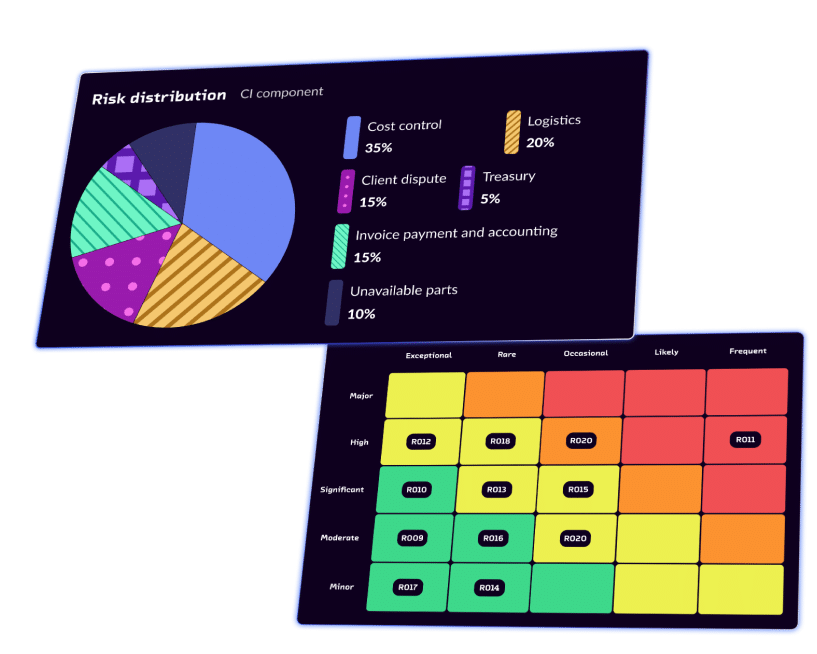
Mappings and KPIs
for optimal management
Anticipate and monitor your risks with interactive mappings and dynamic KPIs.
A powerful tool to monitor and analyze risks in real-time.
📺 Episode 4 - Architecture & KPIs
Discover how ROK enables you to structure and analyze your risks through dynamic mappings and real-time KPIs.
Why choose ROK
for risk management?
A secure and scalable platform to structure, automate, and optimize your audits and risk management.
Security and Compliance
IT Interoperability
Complete Traceability
Flexibility
Fast Deployment
Advanced Management
Go ahead and get started right now!
Learn more: Internal audit automation and risk management
Internal audit automation and risk management: ensure IT traceability and compliance
Internal audit automation and risk management are now central challenges for organizations seeking to ensure digital security and meet regulatory requirements. With integrated tools for advanced internal audit reporting, monitoring, and traceability, companies can effectively manage their security policies and control access to critical resources.
Modern IT governance and compliance systems allow control data to be centralized, anomalies to be identified, and alerts to be triggered automatically. This centralized compliance control is complemented by real-time access monitoring, essential for detecting unusual behavior and ensuring sensitive data protection. When combined with digital identity management, this approach significantly reduces internal vulnerabilities.
Integrating IAM and risk management processes enhances access governance. Separation of duties (SoD), multi-factor authentication, and critical access management all help prevent misuse while maintaining streamlined governance.
This approach naturally fits into a broader hyperautomation strategy (workflow orchestration, BPM, RPA, AI, no-code), which connects access supervision, process automation, and intelligent workflows.
Internal audit automation and risk management: a new approach to security
With internal audit automation and risk management, system monitoring becomes proactive. User behavior analytics tools help quickly identify deviations from standard usage patterns. They integrate with IT intrusion detection and threat analysis mechanisms to strengthen defense layers.
This automation also facilitates the implementation of security policies: rules are enforced systematically, without human dependency, and exceptions are fully documented. Security process automation ensures continuous—not occasional—compliance. Management relies on dynamic reports, with indicators aligned with standards such as GDPR and ISO 27001 compliance.
In case of an alert, security incident management can be triggered automatically, involving stakeholders through predefined workflows. Monitoring of sensitive workflows ensures every action is tracked, validated, and archived. This full orchestration is made possible by BOAT (Business Orchestration and Automation Technologies), which enable seamless coordination between systems, users, and security rules.
Such visibility also relies on clear and dynamic organizational chart management, essential for assigning responsibilities and securing access at every level of the organization.
Internal audit automation and risk management within a broader IT governance strategy
Internal audit automation and risk management are part of a broader enterprise governance strategy. They enable a reduction in cyber risks while improving responsiveness to threats and compliance issues. With dynamic access control tools, the organization can automatically adjust permissions based on role, context, or detected behavior.
Modern solutions also support network vulnerability analysis, identifying potential weaknesses in advance and suggesting automated corrective actions. All of this fits into a continuous management approach, where collected data is cross-referenced to build resilient and scalable information system security.
This infrastructure also helps strengthen communication between IT and business teams by providing shared indicators for more effective collaboration. By aligning operational and regulatory goals, the organization gains a clear vision of its IT governance, driving performance and long-term sustainability.
This logic can be expanded through the Partnership Program and Strategic Partners, opening the platform to a broader ecosystem of technology providers to better address security and compliance challenges.
Finally, in a consistent approach, agile team management plays a complementary role by ensuring a smooth distribution of responsibilities across IT security projects.
Internal audit automation and risk management: a predictive and intelligent vision
Internal audit automation and risk management also enable a predictive approach. By leveraging data from real-time access monitoring, security logs, and detected anomalies, companies can anticipate incidents before they impact operations. This predictive capability relies on data analysis and behavioral intelligence engines that assess trends and recommend actions.
Risk models can be dynamically updated to reflect evolving threats. For example, user behavior analysis can detect suspicious privilege escalation or unusual activity outside regular hours. These weak signals can automatically trigger user isolation, launch an investigation, or temporarily restrict certain accesses.
This level of precision enhances critical access management and supports the implementation of adaptive security policies, where each user is granted only the necessary permissions based on the principle of least privilege. It also actively contributes to network vulnerability management by automatically neutralizing potential attack vectors.
The success of this approach depends on seamless collaboration between business and technical teams. CIOs, CISOs, HR teams, and compliance officers all access personalized dashboards, making information sharing and collective decision-making easier. Thanks to this automation of security processes, organizations improve responsiveness, traceability, and strategic agility.
